HCH Enterprises is ISO 9001:2015 Certified
HCH Enterprises is proud to be ISO 9001:2015 certified, demonstrating our unwavering commitment to delivering exceptional IT and cybersecurity solutions. This prestigious certification validates our dedication to continuous improvement, operational efficiency, and, most importantly, customer satisfaction.
We specialize in a range of IT and cybersecurity services, including managed IT services, cloud security, penetration testing, vulnerability assessments, and incident response.
Our ISO 9001:2015 certification means we adhere to rigorous standards, streamlining our processes to enhance the quality of our IT and cybersecurity services while optimizing resource utilization. This results in cost savings and greater value for our clients. We achieve this through clearly defined quality objectives, a focus on continuous process improvement, and strong management commitment coupled with comprehensive employee training.
Serving clients nationally, HCH Enterprises is your trusted partner for reliable and effective IT and cybersecurity solutions. Contact us today for a free consultation to discuss your specific needs. Book a meeting with us today: BOOK A MEETING
About HCH: HCH Enterprises, LLC (HCH) is a solutions-oriented technology services provider. From managed services to project-based engagements, our IT and Security services allow clients to focus on their core competencies with the peace of mind of knowing their technology framework is operational, optimized, and secure. We are certified as a Minority-Owned, Disabled, and Small Business Enterprise (MBE/DBE/SBE). We believe our work benefits from the diverse perspectives of our employees and are committed to being an Equal Opportunity Employer.
HCH Enterprises (HCH) Attains ITS75 Contract
Five state governments are able to purchase HCH Enterprises’s suite of technology to help public health departments improve programs in their communities
Providence, R.I.–(Press Release) HCH Enterprises, a leading IT and cybersecurity consulting firm focused on managed services and staff augmentation, is pleased to announce its selection as a participating vendor under the Massachusetts ITS75 Software and Services Contract (Category 4). This prestigious designation simplifies the procurement process for public health departments nationwide, enabling them to rapidly adopt HCH’s proven technology solutions and improve community health outcomes.
Benefits for Massachusetts Public Health Departments:
• Faster Deployment: The pre-vetted nature of the ITS75 contract eliminates the need for lengthy procurement procedures, allowing public health departments to implement HCH’s solutions quickly and efficiently.
• Reduced Costs & Risks: Extensive vetting by the Massachusetts Operational Services Division (OSD) ensures HCH meets strict quality and security standards, minimizing risk and streamlining the procurement process.
• Proven Public Health Expertise: HCH has a successful track record of partnering with public health departments nationwide, offering a comprehensive suite of solutions specifically designed for their needs.
HCH’s Capabilities under ITS75:
HCH Enterprises is authorized to provide a wide range of IT services designed to support and enhance public health programs in Massachusetts. These services include:
• Technical Design & Implementation: Our team of experts can assist with designing, implementing, and integrating various software solutions for your public health department.
• Data Management & Workflow Automation: We offer solutions that streamline data management and automate workflows, empowering public health professionals to focus on what matters most – improving population health.
• Cloud Migration & Monitoring: HCH can guide your department through a secure and efficient cloud migration process, ensuring ongoing monitoring and support.
• IT Infrastructure & Security: Our expertise extends to installation, configuration, and ongoing maintenance of IT infrastructure, including multi-factor authentication and DNS filtering solutions.
A Commitment to Public Health Excellence:
HCH Enterprises is dedicated to empowering public health departments with the tools and expertise they need to effectively serve their communities. By leveraging the streamlined procurement process offered by the ITS75 contract, public health departments in Massachusetts can now experience the benefits of HCH’s solutions with greater ease and efficiency.
Ready to Learn More? Contact HCH Enterprises today to discuss how our services can help your public health department achieve its goals.
Who can buy from ITS75? Review the Operational Services Division Award Flyer Here.
About HCH: HCH Enterprises, LLC (HCH) is a solutions-oriented technology services provider. From managed services to project-based engagements, our IT and Security services allow clients to focus on their core competencies with the peace of mind of knowing their technology framework is operational, optimized, and secure. We are certified as a Minority-Owned, Disabled, and Small Business Enterprise (MBE/DBE/SBE). We believe our work benefits from the diverse perspectives of our employees and are committed to being an Equal Opportunity Employer.
Protecting your staff from getting “Hooked”
Small businesses face an ever-present threat: phishing attacks. These deceptive cyber schemes can wreak havoc, leading to data breaches, financial losses, and severe reputation damage. To safeguard your small business and ensure your team stays clear of phishing traps, it’s essential to implement robust security strategies and educate your staff about the dangers of these scams.
Unveiling the Phishing Menace
Phishing attacks involve cybercriminals sending convincing emails or messages that appear to be from trusted sources, often mimicking renowned companies, government entities, or colleagues. The sinister objective? To manipulate recipients into disclosing sensitive information, such as login credentials, credit card details, or personal data, or to dupe them into downloading malicious software.
Safeguarding Your Small Business
Employee Training: Your workforce is the first line of defense against phishing threats. Empower them with the knowledge to spot common phishing indicators, like unexpected emails requesting confidential data, misspelled website URLs, or generic greetings. Encourage a cautious approach and emphasize the importance of verifying unusual requests.
Implement Top-notch Security Software: Get strong antivirus and anti-malware software to protect your computers. Keep this software up to date to make sure it works properly.
Harness Email Filtering: Set up email filters to catch phishing emails before they reach your team. Filters can find and flag suspicious messages, making it harder for phishing attacks to succeed.
Activate Two-Factor Authentication (2FA): Activate Two-Factor Authentication (2FA) for important accounts. This means you’ll need to confirm your identity using a second method, like a text message or an authentication app. It adds a layer of protection.
Regular Updates: Make sure all your software, operating systems, and apps are always up-to-date. Cybercriminals often use weaknesses in outdated software to attack.
Create an Incident Response Plan: Create a plan for what to do if you suspect a phishing attack. The plan should include steps to stop the attack, tell the right people, and investigate what happened.
Embrace Encryption: Use encryption to keep your important information safe. Encrypting emails and files makes it very hard for cybercriminals to steal your data.
Check Your Vendors: If you rely on other companies for services or software, make sure they have strong security measures. A breach at one of your vendors could hurt your business too.
Stay Informed: Stay updated on the latest phishing tricks and trends. Cyber threats change, so it’s important to keep learning to stay safe.
Regular Testing: Regularly test your team with fake phishing emails to see if they can spot them. It helps find areas where more training is needed.
Conclusion
By prioritizing employee education, implementing robust security measures, and staying vigilant, your small business can protect its valuable data and reputation from cybercriminals aiming to get your staff “hooked” in their phishing schemes. Contact HCH Sales to access our support and expertise.
Software Security: A Critical Concern for Businesses in 2025
In March, HCH strongly recommended that clients prioritize addressing the Top 8 Cybersecurity Challenges of 2025. Among these, Software Security emerged as a critical concern, particularly for businesses undergoing Digital Transformation.
The complexity of Software Security is intensified when dealing with Outdated Security Technologies and inadequate responses to Zero Day Events. A valuable approach to bolster Software Security confidence is through Web Application Penetration Testing (WAPT).
Resource Allocation is a Key Concern
A significant overarching concern is resource allocation. Clients with established Software Security processes are striving to achieve more with limited resources. This often involves outsourcing, deferring remediation efforts, and compromising validation processes. Conversely, clients without existing Software Security measures face challenges in securing adequate resources for software development, let alone validation.
HCH acknowledges this dilemma and has chosen to collaborate with CyberLeaf due to their innovative delivery model, which optimizes Return on Investment (ROI) and cost savings for clients.
Instill a Software Security Mindset
Instilling a Software Security mindset within your organization can be transformational. Unlike functional requirements, Security is largely non-functional. While system design, infrastructure configuration, and software coding address functional needs, they might not inherently ensure security. At the very least, development teams should familiarize themselves with the OWASP Top Ten vulnerabilities. CyberLeaf’s assessments have revealed critical vulnerabilities like SQL Injection, Remote Code Execution, and the use of Default Credentials. To effectively address these threats, HCH suggests implementing a comprehensive checklist within your software release process.
Get the Most Out of Your Penetration Testing
To derive maximum value from your investment in penetration testing, it’s essential to empower your penetration tester. Collaborate with HCH to enhance your preparedness. Avoid potential hindrances during testing, such as:
- Testers lacking necessary credentials or access prior to the test initiation.
- Misalignment of the testing scope.
- Insufficient ongoing collaboration throughout the testing process.
- Inadequate brief or asset information.
Remediate and Retest Critical Findings
While CyberLeaf offers retesting for resolved findings, less than 25% of identified issues undergo retesting. Although this might be reasonable for lower-severity findings, it’s concerning that 61% of critical vulnerabilities remain untested again, likely due to unresolved issues or a decision to forgo validating crucial fixes. HCH firmly advocates for the remediation and retesting of critical findings. Moderate findings should not be accepted without formal documentation of compensatory controls.
Conclusion
Trust in your Software Security demands verification. Make security a cornerstone of your software release strategy. Prioritize thorough testing of your software application and adequately prepare for the testing process to maximize its value. Lastly, prioritize the rectification and retesting of significant findings. HCH is dedicated to assisting you throughout this journey. Contact HCH Sales to access our support and expertise.
SecureWorld Boston — Closing Thoughts
By Donald Borsay, Director of Security Solutions, HCH Enterprises
After a prolonged absence due to COVID-19 lockdowns and contract assignments, I was finally able to return to Boston’s Hynes Convention Center for SecureWorld Boston in late March. It was a great opportunity to reconnect with my New England peers, catch up on the latest products and best practices, and even share my thoughts on the next steps of threat intelligence.
I was reassured to see many of my long-lost friends on the speaker list and on the Advisory Council. One of my colleagues pointed out that I had spent two straight hours on the exhibit floor without moving, — as one longtime colleague departed another came. Each of us is busy working hard to tackle cyber risk.
I spent a significant amount of time on the exhibit floor or in special roundtable discussions within the Advisory Council. I learned a lot about the impact of artificial intelligence on cybersecurity and about the recent SEC rulings that may give the Board greater access to the chief information security officer (CISO). I also discovered new products and vendors that are ready to help in the battle for network security.
I had the privilege of leading a threat intelligence panel discussion on “The State of InfoSec Today.” The main takeaway: that with a clear vision, fewer false positives, and continued effort, we can eliminate threats. I offer special thanks to Katherine Chipdey and Jason Albuquerque for the answers and a packed, lively crowd that built upon the seed questions I offered. It takes a village!
When refining your InfoSec program, it’s important to consider how threat intelligence reveals your critical assets’ exposure. Also, be sure that asset vulnerability and remediation are equally prioritized within threat intelligence. If what you have lacks this clarity, seek the capability to add intelligence.
In the threat intelligence arena, it is important to derive both high-level strategic and operational information, as well as low-level technical and tactical information. The devil is in the evolving technical details, so it’s essential to integrate and transform other domains instead of creating threat management silos.
SecurityBeat: Culture Driven Cybersecurity
By Donald Borsay, Director of Security Solutions, HCH Enterprises
At HCH Enterprises, there is no one-size-fits-all approach to cybersecurity. While we all recognize the customs, arts, social institutions, and achievements framed within the culture of a particular country, we likely lack a perspective on cybersecurity. As digital transformation takes over every aspect of our lives, the core enabler remains people. HCH knows how to bring cybersecurity into the culture of your business.
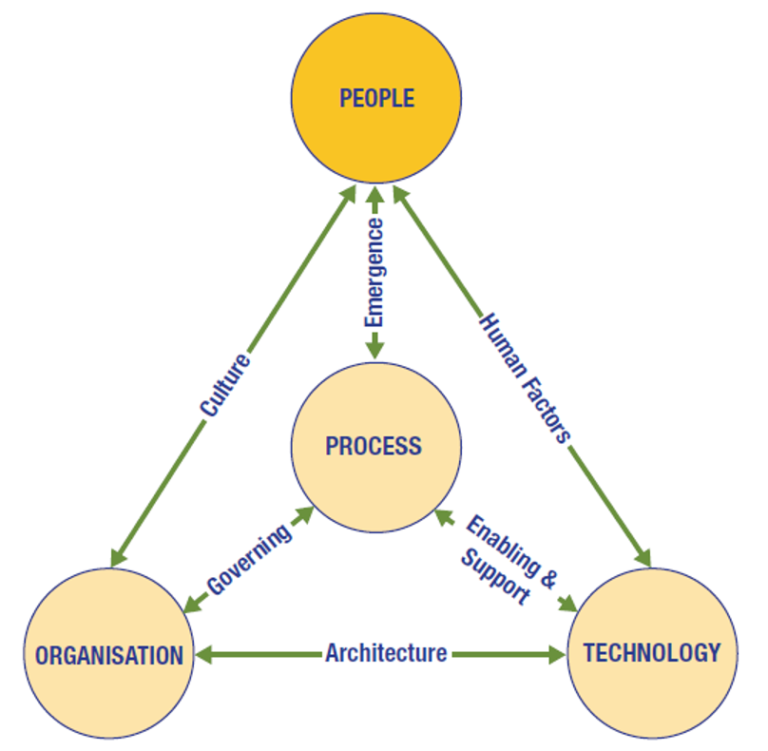
According to ISACA’s The Business Model for Information Security, culture is the first factor that makes cybersecurity part of everything we do. Culture improves through a steady emergence of process. Management recognizes the culture gap and supports incremental advancement. According to the Security Cultures Report from Tessian, the proper security culture directly impacts employee behavior.
The people also use technology directly and must have the skills to support their access and instincts to know when something is wrong. These human factors of technology must be part of the plan. As a result, our People embrace the use of technology and operate it securely by applying their newfound awareness and skills and by following policy and procedure where appropriate.
Sounds good, right? Unfortunately, 45% of users don’t know who to report a security incident to and only 30% of employees believe they play a personal role in cybersecurity. We have so much work ahead of us!
Delivering on the promise of cybersecurity can be a daunting task for high-risk startups, small businesses, and local government when faced with the typical one-size-fits-all toolbox persisted by other providers. HCH’s approach is purposefully tailored to fit your culture. We will partner in your journey to a more mature cybersecurity posture.
SecurityBeat: China 10x U.S. in Cyber Command Staffing
DOJ Prosecutes Individuals Scamming Federal Funding
Ten people have been charged by the U.S. Department of Justice (DOJ) for their alleged roles in business email compromise (BEC) scams. These scams were aimed at a wide range of victims, including federal funding programs like Medicare and Medicaid.
More than $11.1 million was lost as a result of these attacks, with the money stolen by fooling victims into diverting bank transfers to the scammers’ accounts.

Daixin Team Behind Ransomware Attack on AirAsia
A cybercrime group known as Daixin Team has leaked sample data belonging to AirAsia, a Malaysian low-cost airline, on its data leak portal. The threat actors claim that they have access to the personal information of all of the company’s employees and five million passengers. The samples uploaded to the leak site include employee personal information, passenger information, and booking IDs.
The U.S. cybersecurity and intelligence agencies recently issued an advisory about Daixin Team, warning of attacks primarily targeted at the healthcare industry.
Increasing Cyber Risk in the Transportation Industry
Ransomware activity continues to increase globally despite efforts by businesses to boost their cybersecurity. While some industries have doubled or tripled their protection, others are still vulnerable and are finding themselves being targeted by cybercriminals.
According to The Threat Report: Fall 2022 from Trellix, the third quarter of 2022 saw ransomware activity double in the transportation and shipping industry. The report includes evidence of malicious activity linked to ransomware and nation-state-backed advanced persistent threat (APT) actors. It examines malicious cyber activity including threats to email.

China 10x U.S. in Cyber Command Staffing
China’s focus on enhancing its cyber capabilities over the past decade “poses a formidable threat to the United States in cyberspace today,” according to a report released by a congressional advisory commission. The U.S.-China Economic and Security Review Commission’s 2022 Annual Report to Congress assessed a range of threats to the U.S. economy and national security, including Beijing’s cyber warfare and espionage capabilities.
Rackspace’s Hosted Exchange Environment Held Ransom
Four days passed from the time Rackspace disclosed that its customers were experiencing difficulties with the company’s hosted exchange environments until advising that the incident was in fact a ransomware attack. The impairment was promoted to a security incident on day 2 with in-place recovery being so difficult that the company reluctantly notified customers that their email services were migrating to Microsoft 365 on day 4.

Who is Monitoring Your DNS Communications?
For nearly forty years, we stopped manually sharing host information and began relying on the Domain Name Service (DNS) to get the address of the system we need to communicate with. DNS is one of the few protocols we allow to communicate freely without restriction. Why would we need to protect our systems query of the network’s address book?
In a recent report published by Pentera, we find that attackers can use DNS tunneling to communicate with air-gapped networks. Organizations often use air-gapped networks to isolate their sensitive assets.
The takeaway is twofold.
- First, completely air-gap your sensitive assets by disabling DNS and using hostname tables.
- Second, consider using special monitoring solutions to inspect and prevent suspicious DNS traffic from traversing your network.