Grant Opportunity: Connect Your Community
By Chelsea Levesque, Director, Marketing and Communications, HCH Enterprises
In a groundbreaking move, the Broadband Equity, Access, and Deployment (BEAD) program has allocated a staggering $42.45 billion in grants to states, the District of Columbia, and territories. This monumental investment, a key component of the “Investing in America” agenda put forth by the Biden-Harris Administration, aims to provide affordable and reliable high-speed internet access to every American. By bridging the digital divide, this initiative, aptly named “Internet for All,” will reshape our digital landscape, unlocking new opportunities and enhancing competitiveness on a nationwide scale.
Today, high-speed internet is no longer a luxury but a necessity, indispensable for work, education, and healthcare. The “Internet for All” program will enable communities to connect, fostering economic growth and empowering individuals across the country.
Through the allocation of funds, states, the District of Columbia, and territories can establish grant programs specifically designed to deploy or upgrade broadband networks. This critical step ensures that affordable and dependable internet service becomes accessible to everyone.
For comprehensive information on funding allocations tailored to each state, as well as further details on the Biden Administration’s high-speed internet portfolio, we invite you to visit InternetForAll.gov. Stay tuned for the formal allocation notice, which Eligible Entities will receive on June 30, 2023.
At HCH, we are proud to be a part of this transformative initiative. Our organization champions equity and facilitates the grant process for communities. From acquisition to disbursement, we are dedicated to unlocking the full potential of our nation through the power of high-speed internet.
Join us on this journey as we pave the way towards a more connected and inclusive America. Together, we can harness the transformative power of high-speed internet, bringing us closer to a future where opportunities know no bounds.
#InternetForAll #NTIA #InvestingInAmerica #BroadbandEquity #PublicSectorConsulting #ConstituentsFirst #GrantHelp
SecureWorld Boston — Closing Thoughts
By Donald Borsay, Director of Security Solutions, HCH Enterprises
After a prolonged absence due to COVID-19 lockdowns and contract assignments, I was finally able to return to Boston’s Hynes Convention Center for SecureWorld Boston in late March. It was a great opportunity to reconnect with my New England peers, catch up on the latest products and best practices, and even share my thoughts on the next steps of threat intelligence.
I was reassured to see many of my long-lost friends on the speaker list and on the Advisory Council. One of my colleagues pointed out that I had spent two straight hours on the exhibit floor without moving, — as one longtime colleague departed another came. Each of us is busy working hard to tackle cyber risk.
I spent a significant amount of time on the exhibit floor or in special roundtable discussions within the Advisory Council. I learned a lot about the impact of artificial intelligence on cybersecurity and about the recent SEC rulings that may give the Board greater access to the chief information security officer (CISO). I also discovered new products and vendors that are ready to help in the battle for network security.
I had the privilege of leading a threat intelligence panel discussion on “The State of InfoSec Today.” The main takeaway: that with a clear vision, fewer false positives, and continued effort, we can eliminate threats. I offer special thanks to Katherine Chipdey and Jason Albuquerque for the answers and a packed, lively crowd that built upon the seed questions I offered. It takes a village!
When refining your InfoSec program, it’s important to consider how threat intelligence reveals your critical assets’ exposure. Also, be sure that asset vulnerability and remediation are equally prioritized within threat intelligence. If what you have lacks this clarity, seek the capability to add intelligence.
In the threat intelligence arena, it is important to derive both high-level strategic and operational information, as well as low-level technical and tactical information. The devil is in the evolving technical details, so it’s essential to integrate and transform other domains instead of creating threat management silos.
SecurityBeat: Culture Driven Cybersecurity
By Donald Borsay, Director of Security Solutions, HCH Enterprises
At HCH Enterprises, there is no one-size-fits-all approach to cybersecurity. While we all recognize the customs, arts, social institutions, and achievements framed within the culture of a particular country, we likely lack a perspective on cybersecurity. As digital transformation takes over every aspect of our lives, the core enabler remains people. HCH knows how to bring cybersecurity into the culture of your business.
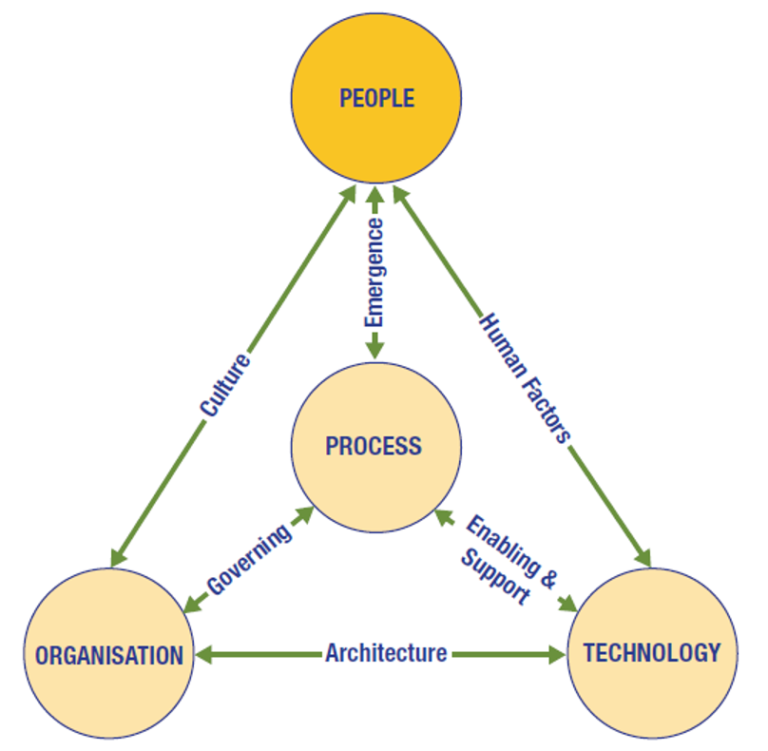
According to ISACA’s The Business Model for Information Security, culture is the first factor that makes cybersecurity part of everything we do. Culture improves through a steady emergence of process. Management recognizes the culture gap and supports incremental advancement. According to the Security Cultures Report from Tessian, the proper security culture directly impacts employee behavior.
The people also use technology directly and must have the skills to support their access and instincts to know when something is wrong. These human factors of technology must be part of the plan. As a result, our People embrace the use of technology and operate it securely by applying their newfound awareness and skills and by following policy and procedure where appropriate.
Sounds good, right? Unfortunately, 45% of users don’t know who to report a security incident to and only 30% of employees believe they play a personal role in cybersecurity. We have so much work ahead of us!
Delivering on the promise of cybersecurity can be a daunting task for high-risk startups, small businesses, and local government when faced with the typical one-size-fits-all toolbox persisted by other providers. HCH’s approach is purposefully tailored to fit your culture. We will partner in your journey to a more mature cybersecurity posture.