Navigating Your ARPA Tech Project Before the 12/31/24 Deadline
The American Rescue Plan Act (ARPA) provided $350 billion in funding for state and local governments to aid in their recovery from the COVID-19 pandemic. This includes funds allocated for rebuilding public sector capacity, which encompasses technology infrastructure.
Here’s what you need to know:
- Deadline: Governments must obligate the funds by December 31, 2024 and spend them by December 31, 2026. Don’t miss out!
- Eligible Uses: You can use ARPA funds to purchase technology to address negative economic impacts, including:
- Rebuilding public sector capacity by rehiring staff or investing in data analysis and technology infrastructure.
- Implementing economic relief programs through tools that manage applications and reports.
- Multi-year contracts: ARPA funds allow for multi-year contracts, giving you peace of mind for your project’s future.
HCH Enterprises can help:
- Navigate ARPA guidelines: We can help you understand the rules and ensure your technology project aligns with eligible uses.
- Develop a strategic plan: We work with you to craft a plan that demonstrates how technology addresses your specific challenges.
- Implement the solution: We offer expertise and resources to ensure successful implementation and continued support.
Additional Resources:
- SLFRF Fact Sheet: https://home.treasury.gov/policy-issues/coronavirus/assistance-for-state-local-and-tribal-governments/state-and-local-fiscal-recovery-funds
How other cities are using their ARPA spend on technology
The National League of Cities, National Association of Counties, and Brookings Institution’s Brookings Metro program have teamed up to create an interactive dashboard that tracks how 152 municipalities are using this relief money. The dashboard allows you to see how cities are investing in a variety of areas, including funding for improving broadband internet access, cybersecurity measures, and tools to help government employees work remotely.
Don’t let this valuable opportunity pass by! Contact HCH today to discuss how we can help your organization leverage ARPA funds for technology solutions.
Protecting your staff from getting “Hooked”
Small businesses face an ever-present threat: phishing attacks. These deceptive cyber schemes can wreak havoc, leading to data breaches, financial losses, and severe reputation damage. To safeguard your small business and ensure your team stays clear of phishing traps, it’s essential to implement robust security strategies and educate your staff about the dangers of these scams.
Unveiling the Phishing Menace
Phishing attacks involve cybercriminals sending convincing emails or messages that appear to be from trusted sources, often mimicking renowned companies, government entities, or colleagues. The sinister objective? To manipulate recipients into disclosing sensitive information, such as login credentials, credit card details, or personal data, or to dupe them into downloading malicious software.
Safeguarding Your Small Business
Employee Training: Your workforce is the first line of defense against phishing threats. Empower them with the knowledge to spot common phishing indicators, like unexpected emails requesting confidential data, misspelled website URLs, or generic greetings. Encourage a cautious approach and emphasize the importance of verifying unusual requests.
Implement Top-notch Security Software: Get strong antivirus and anti-malware software to protect your computers. Keep this software up to date to make sure it works properly.
Harness Email Filtering: Set up email filters to catch phishing emails before they reach your team. Filters can find and flag suspicious messages, making it harder for phishing attacks to succeed.
Activate Two-Factor Authentication (2FA): Activate Two-Factor Authentication (2FA) for important accounts. This means you’ll need to confirm your identity using a second method, like a text message or an authentication app. It adds a layer of protection.
Regular Updates: Make sure all your software, operating systems, and apps are always up-to-date. Cybercriminals often use weaknesses in outdated software to attack.
Create an Incident Response Plan: Create a plan for what to do if you suspect a phishing attack. The plan should include steps to stop the attack, tell the right people, and investigate what happened.
Embrace Encryption: Use encryption to keep your important information safe. Encrypting emails and files makes it very hard for cybercriminals to steal your data.
Check Your Vendors: If you rely on other companies for services or software, make sure they have strong security measures. A breach at one of your vendors could hurt your business too.
Stay Informed: Stay updated on the latest phishing tricks and trends. Cyber threats change, so it’s important to keep learning to stay safe.
Regular Testing: Regularly test your team with fake phishing emails to see if they can spot them. It helps find areas where more training is needed.
Conclusion
By prioritizing employee education, implementing robust security measures, and staying vigilant, your small business can protect its valuable data and reputation from cybercriminals aiming to get your staff “hooked” in their phishing schemes. Contact HCH Sales to access our support and expertise.
Navigating HIPAA Compliance: 10 Vital Pitfalls Health Stewards Must Sidestep
By Chelsea Levesque, Director, Marketing and Communications, HCH Enterprises
In the realm of healthcare, HIPAA (Health Insurance Portability and Accountability Act) stands as a cornerstone for safeguarding patient information. Health stewards, encompassing health insurance companies, HMOs, company health plans, and government programs like Medicare and Medicaid, share the responsibility of upholding HIPAA regulations to preserve patient privacy and maintain data integrity. This blog sheds light on 10 prevalent HIPAA blunders that Health Plans should evade to ensure compliance and cultivate patient confidence.
Neglecting Comprehensive Staff Training:
Mistake: Overlooking the imperative of comprehensive HIPAA training for staff members.
Solution: Implement consistent HIPAA education sessions for your Health Plans team, reinforcing awareness of HIPAA rules, patient privacy, and adept management of sensitive data.
Lax Access Control Measures:
Mistake: Permitting unauthorized personnel unrestricted access to patient records.
Solution: Set up stringent access controls that limit PHI access to authorized personnel exclusively. Regularly assess and refine access authorizations.
Skimming on Risk Assessments:
Mistake: Omitting regular risk assessments that identify potential vulnerabilities.
Solution: Conduct frequent risk assessments to identify potential security loopholes, subsequently applying robust safeguards.
Inadequate Data Storage Security:
Mistake: Storing patient information on unsecured platforms or devices.
Solution: Encrypt electronic PHI (ePHI), implement robust password practices, and adopt secure data storage protocols to thwart unauthorized access.
Poor Data Disposal Practices:
Mistake: Mishandling the disposal of patient data, both physical and digital.
Solution: Enforce secure data disposal techniques, such as shredding paper records and securely erasing electronic data, to prevent unauthorized access post-disposal.
Overlooking Business Associate Agreements:
Mistake: Failing to establish comprehensive agreements with third-party entities handling patient information.
Solution: Draft comprehensive business associate agreements to ensure third-party compliance with HIPAA regulations when handling patient data.
Absence of a Rigorous Incident Response Plan:
Mistake: Operating without a clearly defined plan to manage data breaches and security incidents.
Solution: Develop and regularly update an incident response plan that outlines steps to address potential breaches with prompt and effective measures.
Insecure Communication Channels:
Mistake: Transmitting patient data via unencrypted emails or other insecure modes of communication.
Solution: Employ secure communication methods, such as encrypted email services, to fortify patient data protection during transmission.
Disregarding Patient Rights:
Mistake: Ignoring patients’ rights to access, amend, and request copies of their health records.
Solution: Establish streamlined processes to promptly fulfill patient requests for their health information, respecting their rights diligently.
Insufficient Documentation:
Mistake: Failing to maintain meticulous records of HIPAA compliance efforts.
Solution: Keep detailed records of training sessions, risk assessments, policies, and procedures, ensuring comprehensive documentation to demonstrate compliance when required.
Conclusion
Health stewards bear the onus of upholding patient privacy and adhering to HIPAA regulations. By avoiding these prevalent HIPAA pitfalls and adopting proactive compliance measures, they can secure patient data, bolster patient trust, and shield themselves from potential legal and financial repercussions. Embrace the continuous commitment to HIPAA OSHA compliance, fortifying patient-provider relationships and cultivating a secure environment that benefits both patients and healthcare providers.
We specialize in providing comprehensive OSHA and HIPAA compliance solutions, including certification, tailored to the unique needs of your business. Stay ahead in the compliance game and fortify your commitment to #patient-centric care with us today!
#PublicSectorConsulting #HIPAACompliance #HealthcareIntegrity #PatientPrivacy #HealthPlans #Medicare #Medicaid #HealthInsurance #HMOs #DataSecurity #OSHA
SecurityBeat: Software Security Needs Validating
ncern for Businesses in 2024
In March, HCH strongly recommended that clients prioritize addressing the Top 8 Cybersecurity Challenges of 2024. Among these, Software Security emerged as a critical concern, particularly for businesses undergoing Digital Transformation.
The complexity of Software Security is intensified when dealing with Outdated Security Technologies and inadequate responses to Zero Day Events. A valuable approach to bolster Software Security confidence is through Web Application Penetration Testing (WAPT).
Resource Allocation is a Key Concern
A significant overarching concern is resource allocation. Clients with established Software Security processes are striving to achieve more with limited resources. This often involves outsourcing, deferring remediation efforts, and compromising validation processes. Conversely, clients without existing Software Security measures face challenges in securing adequate resources for software development, let alone validation.
HCH acknowledges this dilemma and has chosen to collaborate with CyberLeaf due to their innovative delivery model, which optimizes Return on Investment (ROI) and cost savings for clients.
Instill a Software Security Mindset
Instilling a Software Security mindset within your organization can be transformational. Unlike functional requirements, Security is largely non-functional. While system design, infrastructure configuration, and software coding address functional needs, they might not inherently ensure security. At the very least, development teams should familiarize themselves with the OWASP Top Ten vulnerabilities. CyberLeaf’s assessments have revealed critical vulnerabilities like SQL Injection, Remote Code Execution, and the use of Default Credentials. To effectively address these threats, HCH suggests implementing a comprehensive checklist within your software release process.
Get the Most Out of Your Penetration Testing
To derive maximum value from your investment in penetration testing, it’s essential to empower your penetration tester. Collaborate with HCH to enhance your preparedness. Avoid potential hindrances during testing, such as:
- Testers lacking necessary credentials or access prior to the test initiation.
- Misalignment of the testing scope.
- Insufficient ongoing collaboration throughout the testing process.
- Inadequate brief or asset information.
Remediate and Retest Critical Findings
While CyberLeaf offers retesting for resolved findings, less than 25% of identified issues undergo retesting. Although this might be reasonable for lower-severity findings, it’s concerning that 61% of critical vulnerabilities remain untested again, likely due to unresolved issues or a decision to forgo validating crucial fixes. HCH firmly advocates for the remediation and retesting of critical findings. Moderate findings should not be accepted without formal documentation of compensatory controls.
Conclusion
Trust in your Software Security demands verification. Make security a cornerstone of your software release strategy. Prioritize thorough testing of your software application and adequately prepare for the testing process to maximize its value. Lastly, prioritize the rectification and retesting of significant findings. HCH is dedicated to assisting you throughout this journey. Contact HCH Sales to access our support and expertise.
Grant Opportunity: Connect Your Community
By Chelsea Levesque, Director, Marketing and Communications, HCH Enterprises
In a groundbreaking move, the Broadband Equity, Access, and Deployment (BEAD) program has allocated a staggering $42.45 billion in grants to states, the District of Columbia, and territories. This monumental investment, a key component of the “Investing in America” agenda put forth by the Biden-Harris Administration, aims to provide affordable and reliable high-speed internet access to every American. By bridging the digital divide, this initiative, aptly named “Internet for All,” will reshape our digital landscape, unlocking new opportunities and enhancing competitiveness on a nationwide scale.
Today, high-speed internet is no longer a luxury but a necessity, indispensable for work, education, and healthcare. The “Internet for All” program will enable communities to connect, fostering economic growth and empowering individuals across the country.
Through the allocation of funds, states, the District of Columbia, and territories can establish grant programs specifically designed to deploy or upgrade broadband networks. This critical step ensures that affordable and dependable internet service becomes accessible to everyone.
For comprehensive information on funding allocations tailored to each state, as well as further details on the Biden Administration’s high-speed internet portfolio, we invite you to visit InternetForAll.gov. Stay tuned for the formal allocation notice, which Eligible Entities will receive on June 30, 2023.
At HCH, we are proud to be a part of this transformative initiative. Our organization champions equity and facilitates the grant process for communities. From acquisition to disbursement, we are dedicated to unlocking the full potential of our nation through the power of high-speed internet.
Join us on this journey as we pave the way towards a more connected and inclusive America. Together, we can harness the transformative power of high-speed internet, bringing us closer to a future where opportunities know no bounds.
#InternetForAll #NTIA #InvestingInAmerica #BroadbandEquity #PublicSectorConsulting #ConstituentsFirst #GrantHelp
Building Inclusive Government Policies: A Roadmap to Equity
Leaders in Government and Critical Infrastructure
Today, we would like to explore how government leaders can champion diversity, equity, and inclusion (DEI) as foundational principles in their decision-making processes. By prioritizing these principles, leaders can create policies that better reflect the needs of all people and build trust among their constituents.
Diversity
Inclusion and representation from various backgrounds, including race, ethnicity, gender, age, abilities, etc.
Equity
Fairness, ensuring that everyone has equal access to opportunities and resources, regardless of their background.
Inclusion
Creating an environment where everyone feels valued, respected, and has a voice in decision-making processes.
Employee Resource Groups (ERGs)
ERGs stand as valuable assets in cultivating inclusive and equitable work environments and communities. They provide a platform for underrepresented employees to connect, gain insights, and advocate for their needs.
ERGs play a pivotal role in DEI initiatives:
Fostering Inclusion: ERGs promote belonging and authenticity among employees, increasing visibility for underrepresented groups and fostering acceptance.
Improving Diversity: ERGs actively participate in talent attraction, showcasing organizations as welcoming communities and communicating the needs of underrepresented groups to leadership.
Promoting External Impact: ERGs assist in recruiting diverse talent pools, diversifying the workforce, and participating in government-led talent attraction events.
Training
Training acts as a catalyst for creating inclusive and equitable environments, addressing individual and institutional aspects.
Key aspects of training in government:
Mitigating Implicit Biases: Training empowers employees to recognize and mitigate unconscious biases in decision-making.
Ongoing Education and Awareness: Training programs keep employees updated on DEI best practices and emerging issues, fostering a culture of continuous improvement.
Interpersonal Relationship Building: Training addresses attitudes, stereotypes, and microaggressions, promoting a respectful workplace.
Institutional Transformation: Training empowers core groups to champion equity initiatives and addresses institutional and structural racism.
Community Engagement
Building connections with diverse community organizations and stakeholders provides invaluable insights into the unique needs and concerns of various populations.
Community engagement is essential for:
Building Relationships and Understanding: Engaging with diverse stakeholders informs policies that truly serve and represent communities.
Enhancing Trust and Transparency: Active listening and collaboration foster trust between government and constituents.
Inclusive Decision-Making: Involving stakeholders in discussions ensures fair and equitable policies.
Effective Service Delivery: Understanding community needs allows for more efficient and equitable service allocation.
Conflict Resolution and Prevention: Open communication helps address issues proactively.
Promoting Civic Participation: Engaging the public encourages active participation in local governance.
State Government Examples

Community-focused racial justice initiatives include:
- Forming a Diversity, Equity, and Inclusion (DEI) task force of community members (State of Rhode Island Diversity, Equity, and Inclusion Department of Administration);
- Celebrating diversity within the community through proclamations and public-facing events (State of Rhode Island DEI Events)
- Designing outreach strategies to include communities that have not been heard or represented (State of Rhode Island Governor’s Workforce Board)
- Rhode Island has made impressive strides in criminal justice reform, partnering with the CSG Justice Center to analyze state data and work alongside the Justice Reinvestment Working Group. Together, they develop data-driven policy options to cut correctional expenses and enhance public safety.
- Rhode Island DEI Leadership pipeline (Rhode Island Foundation Equity Leadership Foundation Initiative 2023/2024 Cohort)

Transparency and Accountability
Transparency and accountability are vital in DEI efforts, driving trust, progress measurement, and positive examples.
Public Trust: Openly sharing DEI goals and progress builds trust with the public.
Stakeholder Engagement: Involving the public and organizations invites collaboration and feedback.
Positive Example: Prioritizing transparency sets an example for other organizations.
The journey towards inclusive government policies involves breaking down barriers, embracing diversity, and promoting fairness at all levels. By implementing ERGs, training, community engagement, and transparency, leaders in government and critical infrastructure can forge a more equitable future for all.
Contributors:
Kathryn Peterson, Technical Writer
Chelsea Levesque, Director, Marketing
References:
- Advancing Racial Equity at the Local Government Level
- Effective employee resource groups are key to inclusion at work
- Commitment to DE&I | Governor’s Work Board
- Transparency and Open Government
- Advancing equity and racial justice through the Federal Government
- Rhode Island Office of Division of Equity Diversity and Inclusion
Gain a comprehensive grasp of effective grant writing and management, along with a deep appreciation for the pivotal role of broadband connectivity, through our enlightening webinar. Designed for professionals in both public and private sectors, this engaging session aims to enhance your knowledge and confidence in navigating the intricacies of grants while fostering the well-being of all communities.
Our interactive webinar delves into the fundamental elements of excelling in grant applications, navigating grant administration, and harnessing the transformative potential of broadband access for community advancement. Whether you’re a dedicated government official, a passionate nonprofit leader, or a knowledgeable private sector consultant, this informative webinar equips you with the essential insights to drive tangible impact within your community and professional sphere.
Webinar Highlights:
– Unveiling the Importance of Grants in Fostering Community Growth
– Exploring the multifaceted benefits of grant funding for nurturing vibrant community development projects
– Real-world case studies illuminating successful, grant-supported projects
– Crafting an Effective Grant Proposal: The Basics
– Navigating Optimal Grant Management Strategies
– Showcasing Achievements of Grant-Supported Broadband Initiatives
– Engaging Q&A Session to Address Your Inquiries
Don’t miss this invaluable opportunity to enhance your grant writing skills, gain insightful perspectives on streamlined grant management tactics, and recognize the life-changing potential of broadband connectivity for diverse communities. Secure your spot today and actively contribute to our mission of empowering communities and fostering sustainable progress.
Register now to embark on a journey towards understanding community empowerment and facilitating enduring growth!
SecureWorld Boston — Closing Thoughts
By Donald Borsay, Director of Security Solutions, HCH Enterprises
After a prolonged absence due to COVID-19 lockdowns and contract assignments, I was finally able to return to Boston’s Hynes Convention Center for SecureWorld Boston in late March. It was a great opportunity to reconnect with my New England peers, catch up on the latest products and best practices, and even share my thoughts on the next steps of threat intelligence.
I was reassured to see many of my long-lost friends on the speaker list and on the Advisory Council. One of my colleagues pointed out that I had spent two straight hours on the exhibit floor without moving, — as one longtime colleague departed another came. Each of us is busy working hard to tackle cyber risk.
I spent a significant amount of time on the exhibit floor or in special roundtable discussions within the Advisory Council. I learned a lot about the impact of artificial intelligence on cybersecurity and about the recent SEC rulings that may give the Board greater access to the chief information security officer (CISO). I also discovered new products and vendors that are ready to help in the battle for network security.
I had the privilege of leading a threat intelligence panel discussion on “The State of InfoSec Today.” The main takeaway: that with a clear vision, fewer false positives, and continued effort, we can eliminate threats. I offer special thanks to Katherine Chipdey and Jason Albuquerque for the answers and a packed, lively crowd that built upon the seed questions I offered. It takes a village!
When refining your InfoSec program, it’s important to consider how threat intelligence reveals your critical assets’ exposure. Also, be sure that asset vulnerability and remediation are equally prioritized within threat intelligence. If what you have lacks this clarity, seek the capability to add intelligence.
In the threat intelligence arena, it is important to derive both high-level strategic and operational information, as well as low-level technical and tactical information. The devil is in the evolving technical details, so it’s essential to integrate and transform other domains instead of creating threat management silos.
Spending ARPA funds. Does your city have a plan?
It’s been nearly two years since the passage of the American Rescue Plan Act (ARPA) — a $1.9 trillion economic stimulus bill including an allocation of $350 billion to help state, local, and tribal governments to address economic and health impacts of the COVID-19 pandemic. While ARPA’s State and Local Fiscal Recovery Fund (SLFRF) dollars offer flexibility, it is important for all municipalities to have a plan in place, and the time to act is now — as cities and towns must obligate their funding by December 31, 2024.
How can municipalities spend SLFRF funds?
Cities and towns have many options for using their ARPA dollars. According to the U.S. Department of the Treasury, there are four separate eligible use categories. Local governments may use SLFRF funds to:
- Replace lost public sector revenue, using this funding to provide government services up to the amount of revenue lost due to the pandemic.
- Respond to the far-reaching public health and negative economic impacts of the pandemic, by supporting the health of communities, and helping households, small businesses, impacted industries, nonprofits, and the public sector recover from economic impacts.
- Provide premium pay for essential workers, offering additional support to those who have and will bear the greatest health risks because of their service in critical sectors.
- Invest in water, sewer, and broadband infrastructure, making necessary investments to improve access to clean drinking water, to support vital wastewater and stormwater infrastructure, and to expand affordable access to broadband internet.
More on SLFRF Rules and Regulations
As a municipality, it’s important to understand how you can use ARPA funding — but that’s only part of the equation. The more challenging element is determining how you should apply these dollars.
The goal for any municipality should be to capitalize on this tremendous opportunity for recovery in ways that meet the most prevalent needs of the community. The challenges many cities and towns face is — identifying those needs, and assessing the most effective pathways to meet those needs. Many communities are developing recovery and growth plans that involve:

- Constituent Communications — engaging with the people in their communities to assess needs and priorities.
- Data Analysis — Collecting, organizing, and analyzing data points to gain insights to accelerate community recovery and equity.
- Peer Evaluation — Reviewing what other similar communities have done and are doing with their ARPA funds, learning from their successes and challenges.
- Compliance and Reporting — Ensuring projects meet the Treasury’s requirements for suitability and that quarterly reporting requirements are met and timely filed.
- Project Management — Defining a plan and developing the roadmap to deliver the intended outcomes.
How are cities and towns using their ARPA money?
As it’s been nearly two years since ARPA’s passing, there is more and more data on how these funds — specifically those of the State and Local Fiscal Recovery Fund — are being allocated. The Council of State Governments published a database of all state-level allocations of SLFRF funding. Additionally, there is a Local Government ARPA Investment Tracker project developed through a partnership between the National League of Cities, Brookings Metro, and the National Association of Counties pulling in data from ARPA projects from cities and counties with populations of at least 250,000.
According to data from the Local Government ARPA Investment Tracker, as of August 31, 2021, 150 local governments submitted 2,577 projects involving $18.5 billion in SLFRF funds. Specifically, these projects involve a number of spending categories:
- Government Operations (37.6%)
- Infrastructure (12.5%)
- Housing (12.5%)
- Community Aid (12.3%)
- Public Health (12.2%)
- Economic and Workforce Development (11.1%)
- Public Safety (2.3%)
While information on how state governments and large cities are deploying their recovery funds is easily accessible, there is very little reporting on how small towns and medium-sized cities are making use of ARPA dollars. That’s why it may be beneficial for small-to-medium cities and towns to work with consultants and project managers to help ensure they are using these SLFRF funds in the most meaningful and efficient ways.
SecurityBeat: Culture Driven Cybersecurity
By Donald Borsay, Director of Security Solutions, HCH Enterprises
At HCH Enterprises, there is no one-size-fits-all approach to cybersecurity. While we all recognize the customs, arts, social institutions, and achievements framed within the culture of a particular country, we likely lack a perspective on cybersecurity. As digital transformation takes over every aspect of our lives, the core enabler remains people. HCH knows how to bring cybersecurity into the culture of your business.
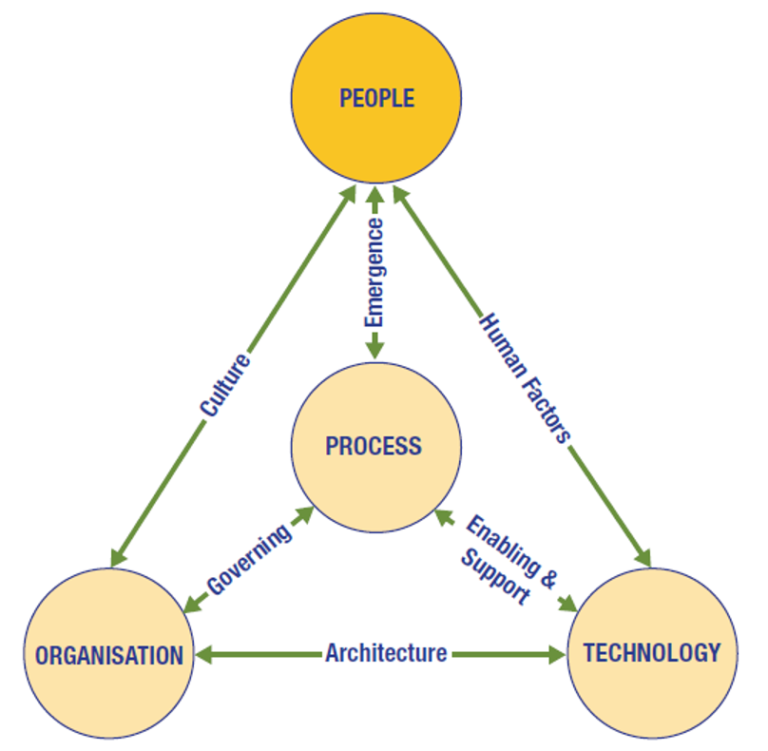
According to ISACA’s The Business Model for Information Security, culture is the first factor that makes cybersecurity part of everything we do. Culture improves through a steady emergence of process. Management recognizes the culture gap and supports incremental advancement. According to the Security Cultures Report from Tessian, the proper security culture directly impacts employee behavior.
The people also use technology directly and must have the skills to support their access and instincts to know when something is wrong. These human factors of technology must be part of the plan. As a result, our People embrace the use of technology and operate it securely by applying their newfound awareness and skills and by following policy and procedure where appropriate.
Sounds good, right? Unfortunately, 45% of users don’t know who to report a security incident to and only 30% of employees believe they play a personal role in cybersecurity. We have so much work ahead of us!
Delivering on the promise of cybersecurity can be a daunting task for high-risk startups, small businesses, and local government when faced with the typical one-size-fits-all toolbox persisted by other providers. HCH’s approach is purposefully tailored to fit your culture. We will partner in your journey to a more mature cybersecurity posture.
